Network security:
Next level monitoring
PRTG monitors firewalls
PRTG monitors ports
PRTG monitors servers
PRTG uses SNMP, NetFlow, and packet sniffing
PRTG maintains the security of your network
Network security with PRTG
Network security: The starting point
Every administrator is faced with the task of developing a central security plan and a security compliance for their company. Part of this plan involves ensuring the various security levels in the firewalls, routers, and switches are properly set. There are network security tools for this purpose, but such tools tend to be extremely expensive.
PRTG is part of your cybersecurity architecture. Our network monitoring software monitors your firewalls, ports, routers, switches, servers, and much more in real-time. With PRTG, you can rest assured that your network is secure. By thoroughly monitoring your hardware, software, VPN connections, and traffic, you’ll quickly identify irregularities and threats in your network. Our motto: Better safe than sorry!
5 practical network security examples:
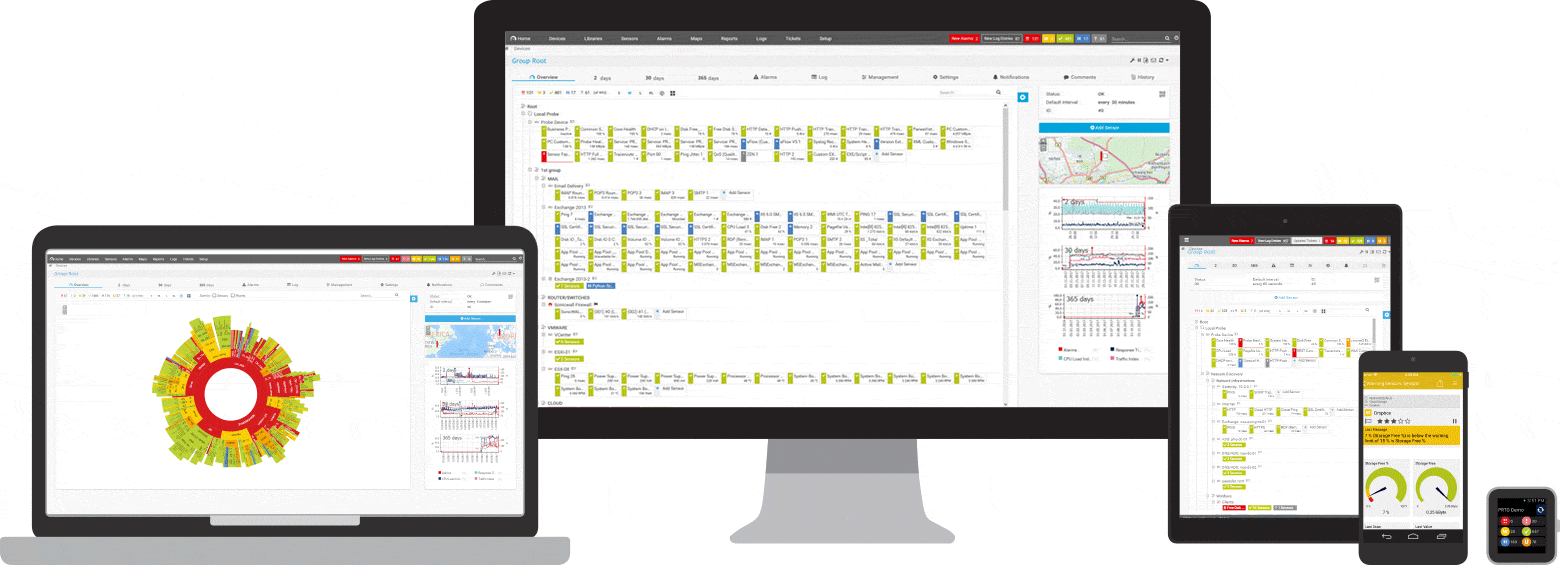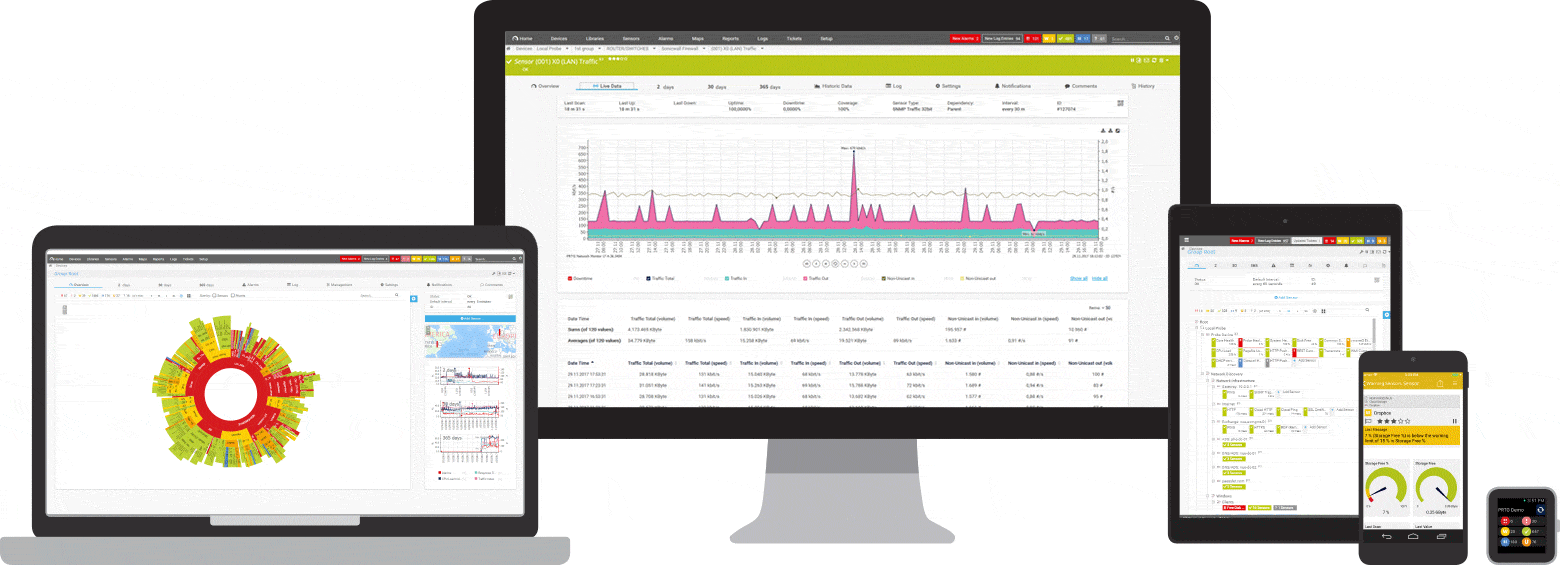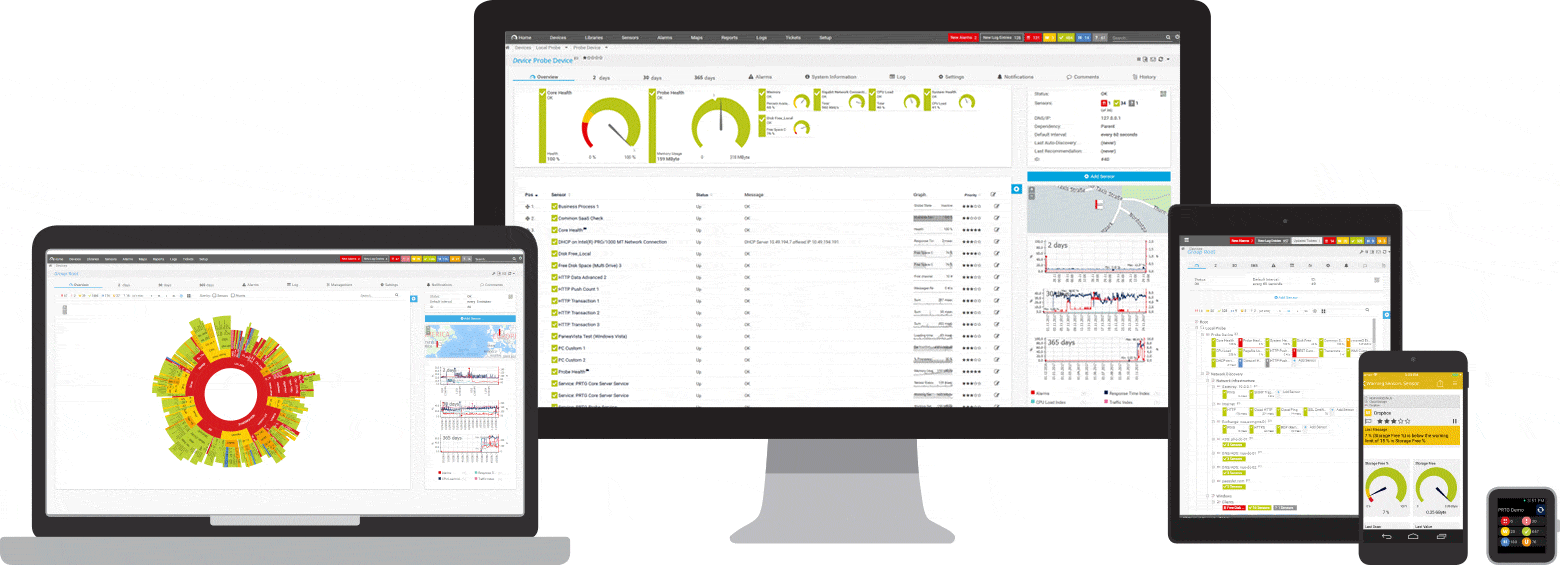
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, e.g. the traffic of a switch port, the CPU load of a server, the free space of a disk drive. On average you need about 5-10 sensors per device or one sensor per switch port. How PRTG defines sensors
Monitoring the firewall
The firewall is the network’s main tool for warding off attacks from the internet. If your firewall is not configured properly or is down, then all gates to your network are open. PRTG immediately lets you know if this is the case so you can quickly take action. To ensure the reliable monitoring of your network, PRTG comes equipped with both SNMP and NetFlow sensors, as well as user-defined sensors such as the HTTP XML/REST Value Sensor. More on firewall monitoring.
NetFlow is a protocol for collecting, aggregating and recording traffic flow data in a network. NetFlow data provide a more granular view of how bandwidth and network traffic are being used than other monitoring solutions, such as SNMP. NetFlow was developed by Cisco and is embedded in Cisco’s IOS software on the company’s routers and switches and has been supported on almost all Cisco devices since the 11.1 train of Cisco IOS Software.
Read more
Unusual traffic
An attack on your IT infrastructure can cause an unusually large amount of data to flow through your network. One of the ways that PRTG picks up on this anomaly is with its Packet Sniffer sensor, which automatically compares values with historical data based on the time of the day and the day of the week. In turn, the software automatically displays an “unusual” status, and sends the administrator an alert so something can quickly be done to fix the problem.
Windows updates
A security loophole exposes your network to hackers all over the world. But not with PRTG: The Windows Updates Status (PowerShell) sensor immediately informs administrators if a new update is necessary, and identifies which network computers are causing security loopholes due to unpatched Windows versions. Windows monitoring not only pays dividends, but also saves an enormous amount of time and frustration.
Open ports
Open ports are necessary, but at the same time dangerous and can lead to vulnerabilities. They are used, for example, to access a network illegally or introduce Trojans. With PRTG, you will always see which TCP ports are open and which ones are closed. This information is vital, for often ports are only used on a temporary basis. Port monitoring lets you work with peace of mind.
Virus scanner update
Even the best antivirus scanner software and malware detector is of no use if it is outdated or down. Use the PRTG WMI Security Center sensor to monitor the status of antivirus software on the clients in your network.
Advantages of monitoring network security with PRTG
A constant eye on software and hardware
PRTG is comprehensive monitoring software that lets you monitor all your software and hardware.
Prompt and customizable alarm
The built-in alarm feature of PRTG is fully customizable. Choose your own threshold values and how you’d like to be informed.
Historical data for comparison
Every PRTG sensor is equipped with an “unusual” sensor status, and will automatically sound the alarm if values emerge which are inconsistent with previous ones. Such values may be indicative of security problems.
Compatibility with all the big manufacturers
PRTG is compatible with all the major software and hardware manufacturers. Along with its custom sensors, PRTG offers special pre-configured sensors for a variety of different manufacturers.
APIs for individual customization
The documented APIs of PRTG allow you to use the monitoring tool for your own individual scenarios. PRTG is therefore perfectly suitable for any network.
A centralized monitoring solution
PRTG is a centralized monitoring tool. Gone are the days of juggling several different tools at once. The central switchboard of PRTG provides the overview you need - not only of your cybersecurity.
Keep a constant eye on your network – even while on the go
Set up PRTG in minutes and use it on almost any mobile device.

Trusted by 500,000 users and recognized
by industry analysts as a leader
“Fantastic network and infrastructure monitoring solution that is easy to deploy and easier still to use. Simply the best available.”
“Software is absolutely perfect, Support is superior. Meets all needs and requirements, this is a must have solution if you are needing any form of monitoring.”
“The tool excels at its primary focus of being a unified infrastructure management and network monitoring service.”

The 5 levels of meta-security
In our meta-security section, we provide detailed information on how to systematically ensure network security and thus create a double layer of protection. Find out more about the five levels of meta-security and how to secure all endpoints here.
PRTG sensors for meta-security
SNMP Custom Sensor
SNMP allows you to monitor the traffic on your devices. The SNMP Custom Sensor can be configured to meet your own specific needs.
Packet Sniffer Sensor
The PRTG Packet Sniffer Sensor lets you monitor traffic in detail. This sensor, too, comes in a customizable version.
WMI Security Center Sensor
Use the PRTG WMI Security Center Sensor to monitor the status of your Windows security tools.
PRTG is a vital tool for getting your IT into tip-top shape!
The costs for a one-year PRTG license pay for themselves in an average of only a few of weeks.
License costs vary according to the size of your network.
Improvement in the reliability of the entire IT
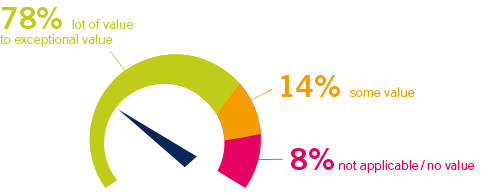
PRTG saves network management costs
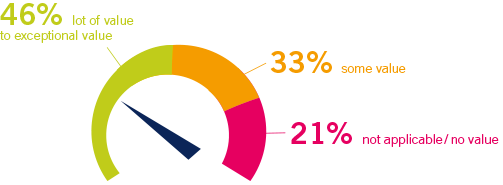
PRTG saves time spent on network management
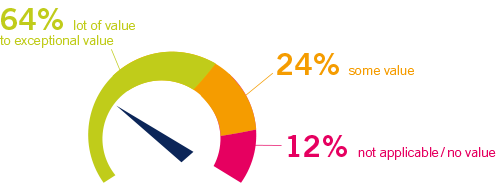
Firewalls: PRTG and the manufacturers
There are many different firewall manufacturers. Administrators are tasked with finding a monitoring tool that can verify that the firewall is online and that it is not displaying any unusual values.
PRTG is compatible with all the major hardware manufacturers, and comes with SNMP, NetFlow, sFlow/jFlow, IPFIX, and other user-defined sensors which can monitor them. You may therefore set up Juniper firewall monitoring, Cisco firewall monitoring, or Dell firewall monitoring – just to name a few.
Other firewall manufacturers, including Barracuda, Checkpoint, Fortinet, gateprotect, F5, Clavister Wolf, and Secure Point, can also be monitored by PRTG, as long as they support a protocol such as SNMP. This you will need to determine on a case-by-case basis.
The PRTG knowledge base contains a few examples: simply enter the name of your firewall manufacturer in the search field and browse the reader questions and articles that are returned. Of course, you can also reach our technical support department directly via the knowledge base, or share your own experience by creating a new thread.
We asked: would you recommend PRTG?
Over 95% of our customers say yes!
Paessler AG conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins.
The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Network security questions
Bandwidth is measured as the amount of data that can be transferred from one point to another within a network in a specific amount of time. Typically, bandwidth is expressed as a bitrate and measured in bits per second (bps). It refers to the transmission capacity of a connection and is an important factor when determining the quality and speed of a network.
Read more
Is network security necessary?
According to a PAESSLER AG survey, identifying and eliminating IT loopholes is one of the main functions of administrators in companies. 58% of those surveyed designated this task as their #1 job. Uptime and ensuring adequate bandwidth came in second and third place in our survey.
How do I get the required budget?
Be sure to present the issue to management in a clear-cut manner so they fully understand the risks. Calculate the cost of downtime beforehand. By doing so, you’ll increase your chances of receiving funds for good hardware and monitoring.
Which network security tools are available?
There are several different network security tools on the market. One of these is Nmap. Although PRTG is inherently not a network security tool, it indirectly serves to keep your network secure. By monitoring your software and hardware, PRTG provides you with an added layer of security. You’ll ensure your network is secure by being “better safe than sorry.” Network security tools range in price, from free to exorbitantly expensive.
Should we perform a penetration test?
Many administrators periodically test their network security by way of paid or internally-executed attacks. A penetration test is useful for detecting possible security loopholes. As a result, you will get a good idea of the areas which can benefit the most from detailed PRTG monitoring.
“Easy to implement and configure with good technical support.”
R. v. S., ICT Manager at Heinen & Hopman Eng BV
You want to know more about other network-related monitoring topics?
Here you find everything about...
PRTG as network traffic analyzer
PRTG: The multi-tool for sysadmins
Adapt PRTG individually and dynamically to your needs and rely on a strong API:- HTTP API: Access monitoring data and manipulate monitoring objects via HTTP requests
- Custom sensors: Create your own PRTG sensors for customized monitoring
- Custom notifications: Create your own notifications and send action triggers to external systems
- REST Custom sensor: Monitor almost everything that provides data in XML or JSON format
Still not convinced?
More than 500,000 sysadmins love PRTG
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Still not convinced?
Monitor your entire IT infrastructure
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Try Paessler PRTG for free
Everyone has different monitoring needs. That’s why we let you try PRTG for free. Start now with your trial.
|
PRTG |
Network Monitoring Software - Version 24.2.94.1400 (April 10th, 2024) |
|
Hosting |
Download for Windows and cloud-based version PRTG Hosted Monitor available |
Languages |
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese |
Pricing |
Up to 100 sensors for free (Price List) |
Unified Monitoring |
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more |
Supported Vendors & Applications |
|









Combining the broad monitoring feature set of PRTG with IP Fabric’s automated network assurance creates a new level of network visibility and reliability.